Welcome To The EPCglobal US Conference & Expo - Los Angeles Convention Center - Image Credit: Edmund Jenks
Welcome To The EPCglobal US Conference & Expo - Los Angeles Convention Center - Image Credit: Edmund JenksRFID Applications Come Into Focus With EPC Standards Overlay
Radio frequency identification is a pretty nifty technology. Take an antenna and some memory, power it up (active) or have it be able to be useful when activated with radio waves (passive) and one has a way to have a greater amount of identification information be attached to an item, a person, or a thing ... Then retrieve this information with proximity based readers without having to have a person to be paid to scan the information (as with barcodes and printed symbology) in order to get it to where it can be used and processed by computer programs.
"Zero human intervention!" stated Peter T. Bloch, RFID Program Director Systemedia Division -
NCR.
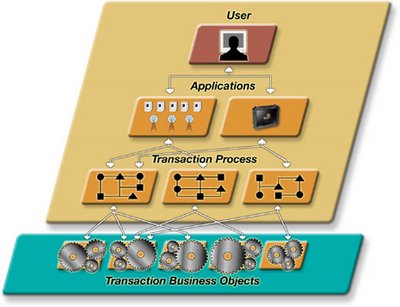 The four steps of creating an Auto-ID or mobility application using ADC involves creating Transaction Business Objects using the more than 80 powerful functions of the platform. Then a business analyst can sequence the Business Objects into a Transaction Process. A group of Transaction Processes are placed together to create an Application and assigned to one or more users. For ADC, a user can be a human or a device, such as an RFID portal. ADC bridges the divide within Auto-ID technologies, providing a platform for intent-based data collection and pervasive data collection. Intent-based data collection ties a person to the Auto-ID process allowing the person to direct when and where data collection activities occur. Pervasive data collection is automated. As materials flow through an environment, movements are captured via RFID tags and readers and processes executed accordingly. Image Credit: NCR/IDVelocity
The four steps of creating an Auto-ID or mobility application using ADC involves creating Transaction Business Objects using the more than 80 powerful functions of the platform. Then a business analyst can sequence the Business Objects into a Transaction Process. A group of Transaction Processes are placed together to create an Application and assigned to one or more users. For ADC, a user can be a human or a device, such as an RFID portal. ADC bridges the divide within Auto-ID technologies, providing a platform for intent-based data collection and pervasive data collection. Intent-based data collection ties a person to the Auto-ID process allowing the person to direct when and where data collection activities occur. Pervasive data collection is automated. As materials flow through an environment, movements are captured via RFID tags and readers and processes executed accordingly. Image Credit: NCR/IDVelocity
Nifty.
As with all efforts designed to help aid in the human endeavor of life, to have this technology maximize the benefit to all, standards must be applied.
Enter the Electronic Product Code (EPC), a number for uniquely identifying an item.
The adoption of this standard and its effect is a little like affixing a wide angle lens to a camera that allows a business effort to visualize, to a greater degree, what is actually happening within the distribution and delivery systems that are set up to fulfill the intended needs of the products we all use.
The application of these standards also allows those who are involved in an activity to meet needs, to think ... Globally.
The conference and expo was "a-buzz" with the anticipation of a breakthrough year in adoption and benefit realization. Truth is, this technology has been growing steadily at about 40% per year (estimated by Joe White, VP Engineering-RFID Tag Business,
Symbol Technologies, Inc.) and still has a few hurdles to overcome before most business processes participate in the benefits of a RFID/EPC standard.
 Symbol Technologies, Inc., The Enterprise Mobility Company, announced that it has launched the RD5000 [09/19/06], a compact, mobile Gen 2 RFID reader that can be integrated with forklifts, pallet jacks, stretch wrappers, and other material handling equipment, and utilized in various space-constrained environments. By extending the range of RFID beyond the dock door, the RD5000 mobile RFID reader provides customers with improved asset visibility in motion throughout the supply chain. Image Credit: Symbol Technologies
Symbol Technologies, Inc., The Enterprise Mobility Company, announced that it has launched the RD5000 [09/19/06], a compact, mobile Gen 2 RFID reader that can be integrated with forklifts, pallet jacks, stretch wrappers, and other material handling equipment, and utilized in various space-constrained environments. By extending the range of RFID beyond the dock door, the RD5000 mobile RFID reader provides customers with improved asset visibility in motion throughout the supply chain. Image Credit: Symbol TechnologiesFor example, currently, not all items are tagged with RFID tags ... let alone tags that conform to the EPCglobal standard. Then, if all items were tagged "globally", there still remains the problem of having hundreds of thousands of portable data collectors that read barcodes but cannot read RFID tags existing in the field. If the people are there anyway, why not give them the ability to capture the RFID data?
"Upgrade them!" says Martin Payne, VP of Marketing & Strategy - Skye Tek. "Sure, upgrade the portable data collectors so that the devices can capture barcodes and RFID as well."
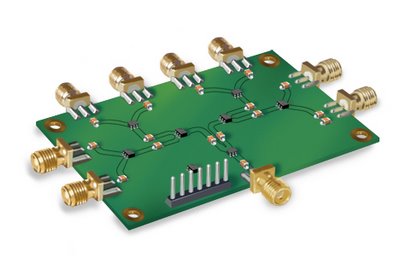 Skye Tek offers the SkyePlus (TM) MXH and MXU antenna multiplexers to ease integration efforts for those devices requiring multiple read-points. Both the MXH and MXU can be equipped with 4 or 8 antenna ports depending on the application requirements. Infrastructure costs are reduced by using the multiplexer to minimize the number of readers required to support multiple read-points. Image Credit: Skye Tek
Skye Tek offers the SkyePlus (TM) MXH and MXU antenna multiplexers to ease integration efforts for those devices requiring multiple read-points. Both the MXH and MXU can be equipped with 4 or 8 antenna ports depending on the application requirements. Infrastructure costs are reduced by using the multiplexer to minimize the number of readers required to support multiple read-points. Image Credit: Skye Tek
Skye Tek, located near Boulder, Colorado, designs and manufacturers RFID reader modules for inclusion with other manufacturers' products. The reason Skye Tek is able to deliver an OEM hardware solution that is smaller and less expensive is because the main load of the technology is shouldered in the software approach that supports the overall RFID information capture solution that Skye Tek delivers. At a cost of inclusion of well under $500.00 per unit, an existing population upgrade can be easily justified when pitted against the information-gathering benefits realized with the addition of multi-technology read capability units working in the field.
As EPCglobal US likes to put it in their "About Us" description -
The EPCglobal Network combines Radio Frequency Identification (RFID) technology, existing communications network infrastructure, and the Electronic Product Code-
TM (a number for uniquely identifying an item) to enable accurate, cost-efficient visibility of information in the supply chain. The end result helps organizations be more efficient, flexible, and responsive to customer needs. To learn more, please visit
http://www.epcglobalus.org/Excerpts from a press release submitted to Business Wire -
EPCglobal US Conference 2006 Puts the Business Value of EPC/RFID in Focus
Senior Executives from Dow Chemical, Procter & Gamble, Wal-Mart, and Wyeth Tell Attendees About Their Companies' Use of Electronic Product Code/Radio Frequency Identification Technology (EPC/RFID)
By Pete Settles, GS1 US - Joanne Beardslee, Elias-Savion - Tuesday, October 17, 2006
LOS ANGELES--(BUSINESS WIRE)--Senior executives representing a broad range of industries addressed 1,300 attendees at the general session of the EPCglobal US Conference 2006 today, discussing how EPC technology is already demonstrating value for their businesses and the potential it has for the future.
"Industries are increasingly turning to EPC/RFID to drive topline business growth, improve product availability, protect supply chains, and reduce supply chain costs," said Mike Meranda, president of EPCglobal US, as he opened the general session.
"The more companies, industries, and trading partners that use this technology, the greater the collective benefits for every company investing in this effort," said Carolyn Walton, vice president of Wal-Mart. "Today, we truly have a realistic opportunity to achieve end-to-end supply chain visibility. We can cut our expenses. We can reduce the concerns about counterfeit products through powerful item identification and authentication. We have the means to create a safer and more secure supply chain. And most important of all - we can do a better job of taking care of our customers."
Thomas Pizzuto, director of RFID technology and strategies at Wyeth spoke about the benefits EPC/RFID brings to the pharmaceutical industry.
"Wyeth views RFID/EPC as an important enabling technology that when combined with other anti-counterfeiting technologies and systems we are implementing will help ensure patient safety and the overall security of the drug supply chain. RFID/EPC gives us the means to mass serialize our products at the item-level and to provide points downstream in the supply chain with a labor-efficient means of identifying and associating these items with their drug pedigree."
"Based on what EPC has done at Procter & Gamble, and how this technology is advancing across a broad range of industries, it is clear this is a transformational initiative," said Dick Cantwell, EPC Team Leader, Procter & Gamble. "We finally have the means to see our products move from the point of production to the point of sale and everywhere in between. Ultimate accuracy, unmatched visibility, real supply chain safety and security - these are no longer things that companies can only imagine. We can achieve them and transform our businesses."Reference Here>>

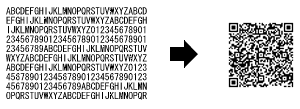
 A QR Code printed 36 feet by 36 feet on a banner and hung on the side of a building in Hiroshima, Japan. Image Credit: PlusD Mobil/IT Media, Inc.
A QR Code printed 36 feet by 36 feet on a banner and hung on the side of a building in Hiroshima, Japan. Image Credit: PlusD Mobil/IT Media, Inc.